Bytesafe: Comprehensive Open Source Security Solution for Software Supply Chain Management
Continuous Integration SoftwareBytesafe provides a comprehensive platform for managing open source threats, featuring a Dependency Firewall and Software Composition Analysis to ensure software supply chain security.
About Bytesafe
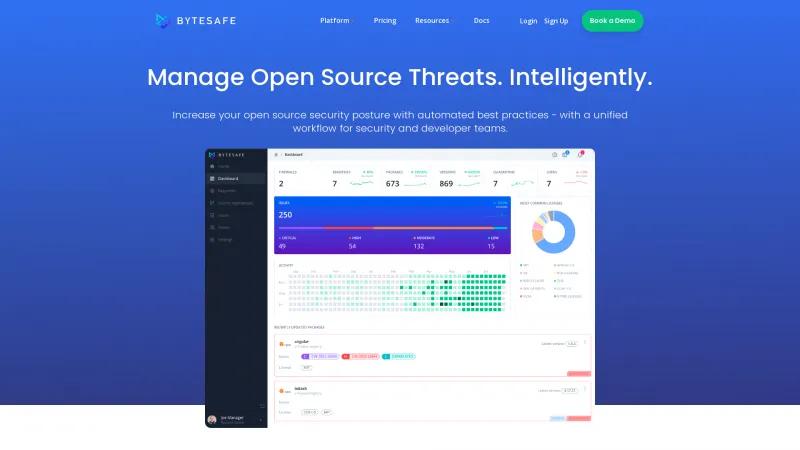
Bytesafe offers an exceptional solution for managing open source threats, providing a comprehensive platform that ensures end-to-end security across the software supply chain. Their innovative approach to security is particularly noteworthy, as it intelligently integrates automated best practices into a unified workflow that benefits both security and development teams.
The standout feature, the Dependency Firewall, effectively quarantines malicious open source components before they can reach developers, safeguarding critical data and maintaining the integrity of company assets. This proactive measure, combined with a robust policy engine that evaluates various threat signals, positions Bytesafe as a leader in the realm of software supply chain security.
Moreover, the Software Composition Analysis (SCA) tool provides invaluable insights into the open source components utilized within applications, allowing organizations to avoid exploitable vulnerabilities. The automatic tracking of license compliance issues further enhances the platform's utility, ensuring that businesses remain compliant with open source licenses and avoid potential legal pitfalls.
Clients have praised Bytesafe for its high availability and seamless integration into CI/CD pipelines, highlighting its effectiveness in maintaining the security of private packages. The testimonials from CTOs underscore the platform's reliability and the peace of mind it brings to organizations navigating the complexities of open source software.
Bytesafe is not just a tool; it is a vital partner in enhancing open source security posture. For any organization looking to fortify its software supply chain against emerging threats, Bytesafe is undoubtedly a solution worth considering.
DevOps Features
- Approval Workflow
- Prioritization
Continuous Integration Features
- Continuous Delivery
- Continuous Deployment
Source Code Management Features
- Collaboration
- Continuous Integration
Vulnerability Scanners Features
- Compliance Monitoring
- Continuous Monitoring
- Logging and Reporting
Vulnerability Management Features
- Prioritization
Leave a review
User Reviews of Bytesafe
No reviews yet.